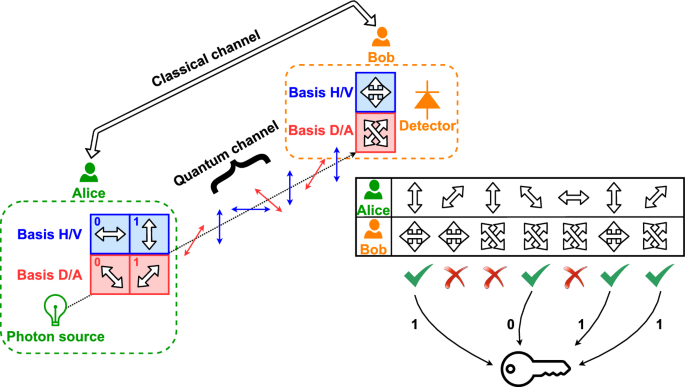
Implementation of BB84 protocol using three bases. The distance between... | Download Scientific Diagram

Running Feature: Quantum Key Distribution, Protecting the Future of Digital Society (Part 1) The Principles of Quantum Key Distribution Technology and the BB84 Protocol | DiGiTAL T-SOUL | TOSHIBA DIGITAL SOLUTIONS CORPORATION
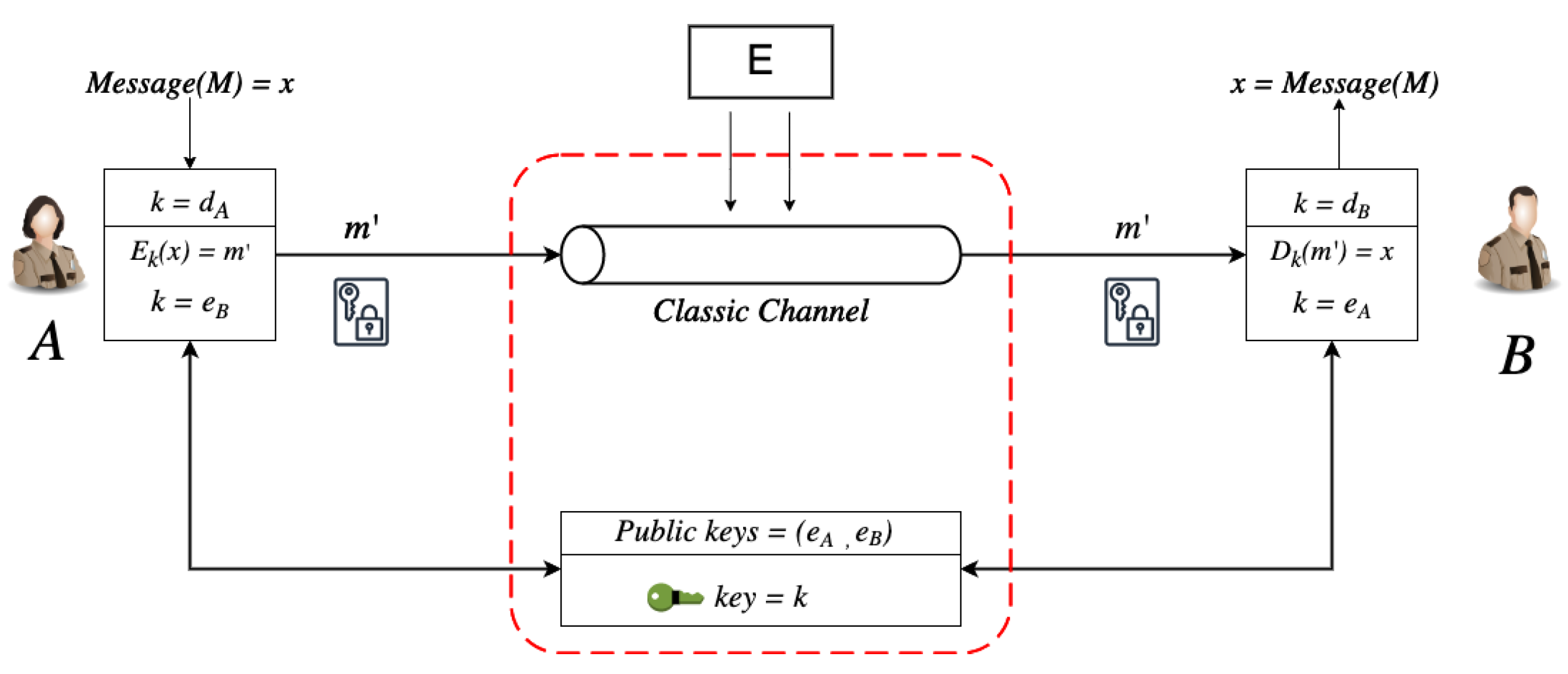
Sensors | Free Full-Text | Quantum Key Distribution: Modeling and Simulation through BB84 Protocol Using Python3
1: Working principle of the BB84 protocol. Alice uses two conjugated... | Download Scientific Diagram

Running Feature: Quantum Key Distribution, Protecting the Future of Digital Society (Part 1) The Principles of Quantum Key Distribution Technology and the BB84 Protocol | DiGiTAL T-SOUL | TOSHIBA DIGITAL SOLUTIONS CORPORATION

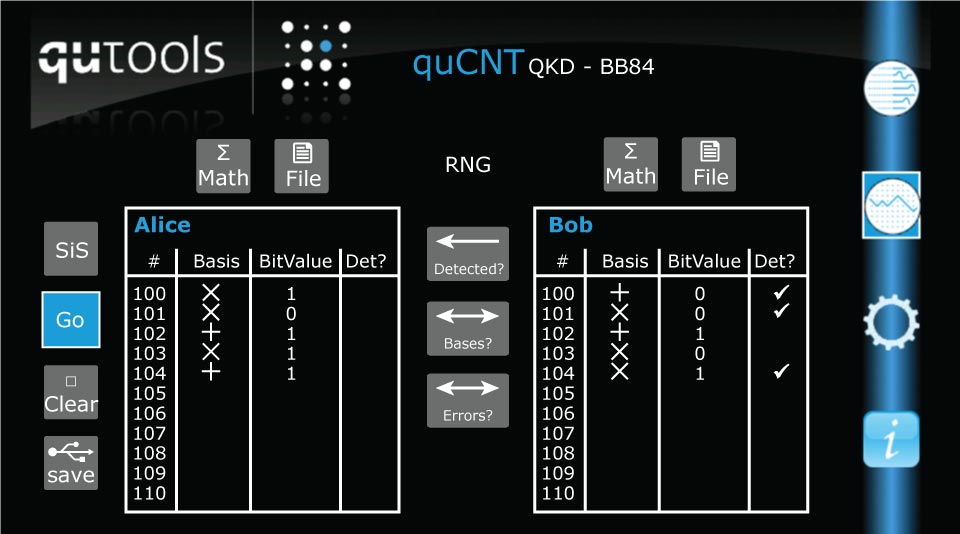
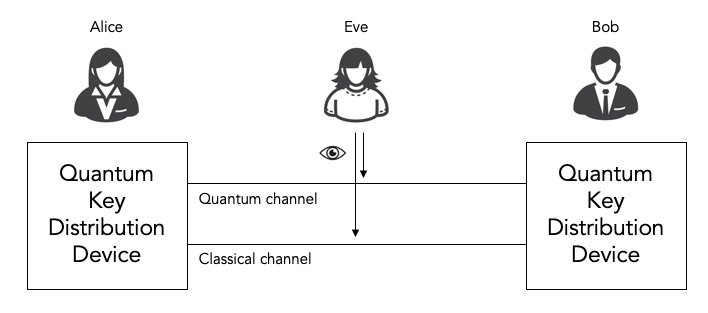
![PDF] Simulation of BB 84 Quantum Key Distribution in depolarizing channel | Semantic Scholar PDF] Simulation of BB 84 Quantum Key Distribution in depolarizing channel | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dadec5fec103285dd0dcc77bdab01714746f18d0/1-Table1-1.png)